Securing your PBX Phone System
Securing your PBX Phone System out of the box once installed is one of the first things you must do.
As with most business network devices - when you first install your phone system - set it up on a "Static IP Address". We recommend doing this in your DHCP assignment device - rather than in the PBX device itself. This solves other network headache issues that can come up later on.
Most systems come with "standard default" settings and login credentials out of the box, and are not secure enough for most business password policies.
This means changing both the "Default" administrator password, and changing device service ports to ensure "Standard Industry Ports" are not being used once you're system is full configured.
Also make sure ALL your devices are behind a firewall / router with strong or strict security methodology.
It is also important to ensure you have the latest firmware installed on your phone system. Check for firmware updates regularly, and install them as new versions are released. You should double check the firmware version on your system before doing any initial configuration.
Administrator Password Changes
In most systems you can create both a "New Super-Administrator" username and change the default password that comes with your phone system.
As many devices are different - you should check your user admin manual or contact SPB for information how to change the default admin username.
Change and use 16 or more mixed characters for your new Super-Administrator password.
In some cases, systems usually come with a 6 to 8 character or digit default password printed on a label on the bottom of the device. This is not secure enough for a SIP based device environment.
Ensure you use STRONG PASSWORDS with mixed alpha-numeric and special characters (such as: #$%^&!+=-)
If the manufacturers' firmware allows it - in most cases in today's industry - they do. Take advantage of this feature and store your Super-Admin and Password in a secure place.
Set-up "User level Administrator" access separate from your main Super-Admin credentials.
This ensures other users can't accidentally overwrite Super-Admin credentials and in most cases, User Level Administrators can also be restricted from accessing or making changes to the system configuration, if you want to restrict them to only a certain limited amount of feature access.
Changing Default Industry PBX System Ports
Many IP based phone systems on the market come with standard industry ports enabled. This includes both "Admin webGUI" access port, and SIP / VoIP transport ports (used for both registration and voice traffic communication protocols).
***Check with your user manual and / or SBP when attempting to change ports as changing them may cause your system to become unstable in both a set-up and working environment.
You also need to be careful which ports to change to. Check with IANA.org for a complete list of ports assignments registered and used by many systems all over the world. For best security - use only ports which are "not actively assigned" so the port doesn't conflict with other hardware and software services currently in use.
Http / Https Standard Administration Port:
In some systems there is a standard port, such as TCP Port: 8089 or port 443, which is used to forward users to the administration login page. This is one of the first things you should do. We recommend changing to a higher range port for the administrator panel. In the case of both these ports - there are many other devices on the market which can also use those ports on your network for login pages as well.
Change the admin ports to use a higher number, example: 21850-21999 'Currently "Unassigned"' as listed by IANA.org.
So using port 21982 as example, can be used as your "hidden administration page port". You will then login to your system's admin page using an internal network port IP Address - Eg.: https:// 192.168.1.200:21982
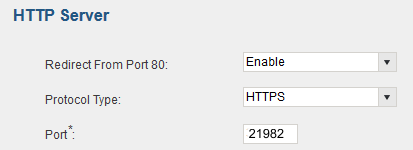
You can then use this hidden port for both internal network system access and for remote access, since it is an uncommon port. You would need to map your firewall / router port settings to map to 21982 from the WAN and use your public IP address at the PBX location + the ":21982" to access your system.
*Note: In above example screen shot - Port 80 will ONLY work on your local network. It will not work from WAN remote access unless you set-up the port forwarding rule in your router/firewall for port 80 to the system IP address (NOT recommended anyways, since it's a standard port, yet again!)
Change Default UDP SIP Ports used for SIP Registration
MOST manufacturers of IP-PBX Phone System still set-up up the default SIP UDP port 5060 as this is the industry standard port for SIP registrations between: VoIP service providers, your main telephone device and client (desk phones/cordless phones).
If you are intending on using any external network services like VoIP Telephone Trunking, or 'remote extensions for remote office workers' - we HIGH RECOMMEND changing the standard default SIP port right away.
The problem with the industry standard SIP port is there are automated scanning servers around the world that attempt to infiltrate online PBX devices using port scanning method on "well known ports".
To save yourself time and energy when your system is online - change the default SIP port right away to another "unlisted port" for SIP transport. IE: Sometimes it is enough to change from port 5060 (UDP) to port 6089.
**This reduces the attempted 'automated SIP port scan internet servers' from trying to register to your main system over and over again.
But, in some cases even moving to a higher SIP transport port may be desired by the site administrator, if your supporting SIP Service Provider allows for it. You should also ensure you use strong client device "authentication methods (SIP username / passwords). We will touch on this in another article on our SBP Tips page.
A final word on initial security policies
It is important to use a good business or higher end class of home router for your network. Using one with good firewall set-up and policies is best. Many lower end and ISP routers do not have the correct firewall firmware implemented in their devices - so spend a little extra on your router or firewall network infrastructure.
Always check for firmware updates and regularly apply them. FYI - We ourselves like, and use, ASUS brand of routers. They have ample set-up for most home based and small business uses. Some of the higher priced ($199.99 and up) ASUS routers also have mobile phone or reminder feature that a "new firmware is available" when you login to the router. So you can always apply the router manufacturer's firmware updates on a regular basis.



